Scenario
An after-hours alert from the Endpoint Detection and Response (EDR) system flags suspicious activity on a Windows workstation. The flagged malware aligns with the Amadey Trojan Stealer. Your job is to analyze the presented memory dump and create a detailed report for actions taken by the malware.
Artifacts
Windows 7 x64-Snapshot4.vmem
Q1
In the memory dump analysis, determining the root of the malicious activity is essential for comprehending the extent of the intrusion. What is the name of the parent process that triggered this malicious behavior?
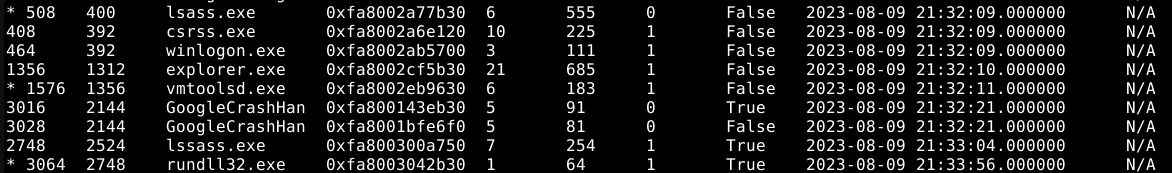
Using volatility to examine the process tree using
python3 vol.py -f 'Windows 7 x64-Snapshot4.vmem' windows.pstreewe can start looking for any unusual processes. Looking through one particular process stands outlssass.exe.While lsass.exe is a legitimate process, we can quickly tell that this process is not normal as it has an extra S.
Q2
Once the rogue process is identified, its exact location on the device can reveal more about its nature and source. Where is this process housed on the workstation?
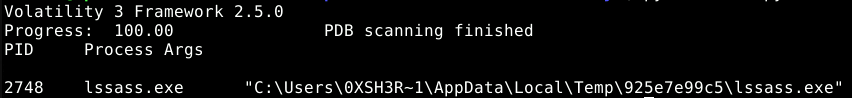
Now that we know what process we are looking for, we can check use
windows.cmdlineto look at the command line arguments of the processes. using--pid 2748we can filter it down to the specific process we are looking for.We find that the process was launched from
C:\Users\0XSH3R~1\AppData\Local\Temp\925e7e99c5\lssass.exe
Q3
Persistent external communications suggest the malware’s attempts to reach out C2C server. Can you identify the Command and Control (C2C) server IP that the process interacts with?
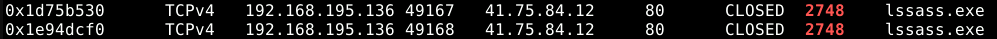
To find this information, we can use the
windows.netscanplugin to list network artifacts. Looking at the output PID 2748 lssass.exe can be found having had a connection to41.75.84.12.
Q4
Following the malware link with the C2C, the malware is likely fetching additional tools or modules. How many distinct files is it trying to bring onto the compromised workstation?
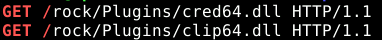
Using the windows.memmap command specifying pid 2748, we can dump the contents to try and extract any information on downloaded files. Once the dump is complete, strings can be used to search for any downloads.
strings pid.2748.dmp | grep "GET /"
Q5
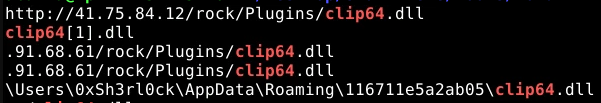
Identifying the storage points of these additional components is critical for containment and cleanup. What is the full path of the file downloaded and used by the malware in its malicious activity?
Expanding on the previous search, we can again use strings to look for the downloaded files.
Q6
Once retrieved, the malware aims to activate its additional components. Which child process is initiated by the malware to execute these files?
Looking back at windows.pstree, we can look at process that have been created by our original malicious process. Having found that a malicious .dll file was downloaded, we can safely assume that rundll32.exe will be used. Our suspicion is confirmed by the output of pstree.
Q7
Understanding the full range of Amadey’s persistence mechanisms can help in an effective mitigation. Apart from the locations already spotlighted, where else might the malware be ensuring its consistent presence?
Having previously found the malicious dll files, it is important to find any persistence the malware may have established. We have already found the original location of the lssass.exe file in the Temp directory. In order to determine if it is located anywhere else, the
windows.filescanplugin can be used to attempt to locate any further matches.python3 vol.py -f '/home/ubuntu/Desktop/Start here/Artifacts/Windows 7 x64-Snapshot4.vmem' windows.filescan | grep "lssass"