Scenario
Adversaries may use a single or small list of commonly used passwords against many different accounts to attempt to acquire valid account credentials. Password spraying uses one password (e.g. ‘Password01’), or a small list of commonly used passwords, that may match the complexity policy of the domain. Logins are attempted with that password against many different accounts on a network to avoid account lockouts that would normally occur when brute forcing a single account with many passwords.
Typically, management services over commonly used ports are used when password spraying. Commonly targeted services include the following:
SSH (22/TCP)
Telnet (23/TCP)
FTP (21/TCP)
NetBIOS / SMB / Samba (139/TCP & 445/TCP)
LDAP (389/TCP)
Kerberos (88/TCP)
RDP / Terminal Services (3389/TCP)
HTTP/HTTP Management Services (80/TCP & 443/TCP)
MSSQL (1433/TCP)
Oracle (1521/TCP)
MySQL (3306/TCP)
VNC (5900/TCP)
In addition to management services, adversaries may “target single sign-on (SSO) and cloud-based applications utilizing federated authentication protocols,” as well as externally facing email applications, such as Office 365.[
In default environments, LDAP and Kerberos connection attempts are less likely to trigger events over SMB, which creates Windows “logon failure” event ID 4625.
Q1
Who was the last logged-in user?
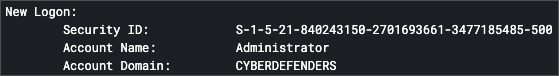
The Windows Event ID 4624 is associated with successful logins. Using the query
event.code: 4624and sorting by New to Old, you will find that the last logged in user wasAdministrator
Q2
What is the logon type of the failed logons?
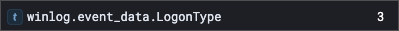
The Windows Event ID 4625 is associated with failed logins. Using the query
event.code: 4625will reveal that the logon type is3which is a network logon.
Q3
What is the protocol the attacker tried to bruteforce?
Viewing the surrounding documents of one of the failed attempts shows reference to RemoteDesktopServices. With this information in mind, using the following search can help confirm the brute force attempt.
message: 192.168.1.60 and winlog.provider_name: "Microsoft-Windows-RemoteDesktopServices-RdpCoreTS"The results look to confirm that the protocol being brute forced isrdp
Q4
How many users did the attacker succeed in getting their accounts?
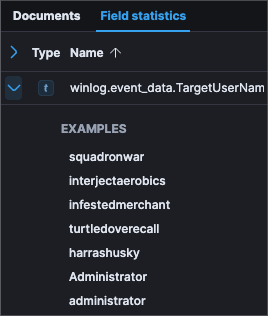
Going back to looking at successful logins, filtering for
message: 192.168.1.60 and event.code: 4624reveals 8 documents. Examining the contents of the message you will find that6accounts were compromised and successfully logged into. Alternatively the Field statistics can be viewed using the field winlog.event_data.TargetUserName
Q5
According to Microsoft. What is the description of the “Sub Status” code for event id 4625?
Querying for
event.code: 4625and selecting one of the brute force attempt logs, perform a web search for the winlog.event_data.SubStatus code0xc000006aalong with the event ID 4625. The search should lead you to Microsofts Learn documentation where you will find the answerUser logon with misspelled or bad password
Q6
How long did the bruteforce last? MM:SS
Using the query
message: 192.168.1.60 and event.code: 4625select the Field statistics and add the @timestamp field. Expanding this field you will find the earliest time atAug 1 2022, 16:29:09.460and the latest time atAug 1 2022, 16:34:57.623Quick calculations will show the attack lasted for05:48
Q7
How many minutes passed before the attacker logged into the machine again?
Using the query
message: 192.168.1.60 and event.code: 4624the brute force appears to have stopped following the 6 accounts that were compromised at16:34:57The next successful login is using the Administrator account at16:46:09. The difference between the two is 11 minutes and 12 seconds. As the question is looking only for minutes, the answer is11.
Q8
What is the name of the policy used to lock the account after a certain number of failed login attempts?
Performing a web search for Windows policies, the policy
Account Lockoutwill be found.