[CyberDefenders] Volatility Traces
Scenario
On May 2, 2024, a multinational corporation identified suspicious PowerShell processes on critical systems, indicating a potential malware infiltration. This activity poses a threat to sensitive data and operational integrity.
You have been provided with a memory dump (memory.dmp) from the affected system. Your task is to analyze the dump to trace the malware’s actions, uncover its evasion techniques, and understand its persistence mechanisms.
Artifacts
memory.dmp
Q1 - Process Name
Identifying the parent process reveals the source and potential additional malicious activity. What is the name of the suspicious process that spawned two malicious PowerShell processes?
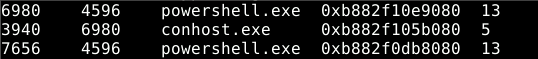
The PPID of the two powershell processes can be found using the
pslistplugin. The ID in the second column is the PPID.
The parent process is not visible, so to try and find the parent process the
psscanplugin can be used to find hidden or inactive processes.
The full name of the process isn’t visible due to the way data is stored in memory. Process names are often truncated because memory structure only allocates space for the first 16 characters. We can attempt to retrieve the full name of the process by using the
cmdlineplugin, which examines the command line used to start the process, potentially providing the full name or additional information about the malicious process. Examining the output the malicious executable is visible from the powershell process with PID 6980.
Q2 - Executable responsible
By determining which executable is utilized by the malware to ensure its persistence, we can strategize for the eradication phase. Which executable is responsible for the malware’s persistence?
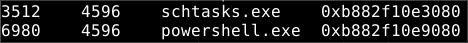
Examination of the
psscanplugin results reveals that several other tasks, includingschtasks.exe, share the parent process ID 4596. This suggests a common persistence technique: using a scheduled task to ensure the malicious executable runs at startup or login.
Q3 - Other process
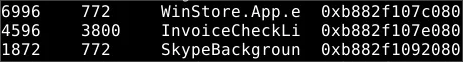
Understanding child processes reveals potential malicious behavior in incidents. Aside from the PowerShell processes, what other active suspicious process, originating from the same parent process, is identified?
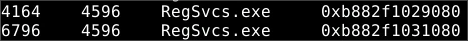
As before, examining parent process ids reveals that
RegSvcs.exewas also spawned by the same malicious process.
Q4 - PowerShell cmdlet
Analyzing malicious process parameters uncovers intentions like defense evasion for hidden, stealthy malware. What PowerShell cmdlet used by the malware for defense evasion?
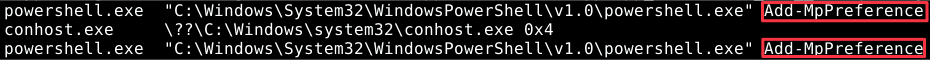
Referring to the previous
cmdlineplugin results, you’ll notice that the attacker usedAdd-MpPreferenceto exclude two executables from being scanned by Windows Defender.
Q5 - Malware exclusion
Recognizing detection-evasive executables is crucial for monitoring their harmful and malicious system activities. Which two applications were excluded by the malware from the previously altered application’s settings?
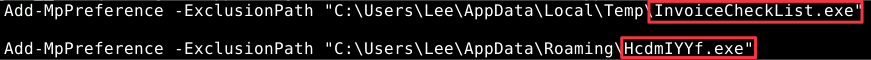
Examining the
cmdlineplugin results show that HcdmIYYf.exe and InvoiceCheckList.exe were added to the exclusion list for Defender
Q6 - MITRE sub-technique
What is the specific MITRE sub-technique ID associated with PowerShell commands that aim to disable or modify antivirus settings to evade detection during incident analysis?
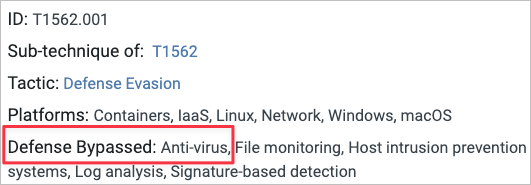
Utilizing the ATT&CK Matrix you will find the tactic under Defense Evasion → Impair Defenses. The specific tactic in this case is
T1562.001, Disable or Modify Tools
Q7 - Linked account
Determining the user account offers valuable information about its privileges, whether it is domain-based or local, and its potential involvement in malicious activities. Which user account is linked to the malicious processes?
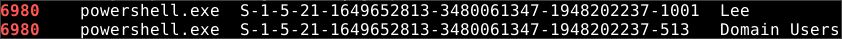
By using the
getsidsplugin, you can identify the user associated with a specific process. To narrow down the search, you can use thegrepcommand to filter results by a particular PID. Examining the results, the userLeecan be identified as the process owner